Section 2 – Implement a Security Extension of a Layer 2 solution, given a network design and a set of requirements
QUESTION NO: 1
You need to configure port security on switch R1. Which two statements are true about this technology? (Select two)
A. Port security can be configured for ports supporting VoIP.
B. With port security configured, four MAC addresses are allowed by default.
C. The network administrator must manually enter the MAC address for each device in order for the switch to allow connectivity.
D. With port security configured, only one MAC addresses is allowed by default.
E. Port security cannot be configured for ports supporting VoIP.
Answer: A,D
Explanation:
You can use the port security feature to restrict input to an interface by limiting and identifying
MAC addresses of the workstations that are allowed to access the port. When you assign secure MAC addresses to a secure port, the port does not forward packets with source addresses outside the group of defined addresses. If you limit the number of secure MAC addresses to one and assign a single secure MAC address, the workstation attached to that port is assured the full bandwidth of the port.
This feature is indeed supported on voice VLAN ports. If you enable port security on a port configured with a voice VLAN and if there is a PC connected to the CiscoIPPhone, Cisco tells us to set the maximum allowed secure addresses on the port to at least 3.
QUESTION NO: 2
Refer to the exhibit. The show port-security interface fa0/1 command was issued on switch SW1. Given the output that was generated, which two security statement are true? (Choose two.)

A. Interface FastEthernet 0/1 was configured with the switchport port-security aging command.
B. Interface FastEthernet 0/1 was configured with the switchport port-security protect command.
C. Interface FastEthernet 0/1 was configured with the switchport port-security violation restrict command.
D. When the number of secure IP addresses reaches 10, the interface will immediately shut down.
E. When the number of secure MAC addresses reaches 10, the interface will immediately shut down and an SNMP trap notification will be sent.
Answer: B,E
Explanation:
Port security is a feature supported on Cisco Catalyst switches that restricts a switch port to a specific set or number of MAC addresses. Those addresses can be learned dynamically or configured statically. The port will then provide access to frames from only those addresses. If, however, the number of addresses is limited to four but no specific MAC addresses are configured, the port will allow any four MAC addresses to be learned dynamically, and port access will be limited to those four dynamically learned addresses.

When Switch port security rules violate different action can be applied:
1. Protect: Frames from the nonallowed address are dropped, but there is no log of the violation.
2. Restrict: Frames from the nonallowed address are dropped, a log message is created, and a Simple Network Management Protocol (SNMP) trap is sent.
3. Shutdown: If any frames are seen from a nonallowed address, the interface is errdisabled, a log entry is made, an SNMP trap is sent, and manual intervention or errdisable recovery must be used to make the interface usable.
The port will not be shutdown, because it is in protect mode — not shutdown.
QUESTION NO: 3
A Company switch was configured as shown below:
switchport mode access
switchport port-security
switchport port-security maximum 2
switchport port-security mac-address 0002.0002.0002
switchport port-security violation shutdown
Given the configuration output shown above, what happens when a host with the MAC address of 0003.0003.0003 is directly connected to the switch port?
A. The host will be allowed to connect.
B. The port will shut down.
C. The host can only connect through a hub/switch where 0002.0002.0002 is already connected.
D. The host will be refused access.
E. None of the other alternatives apply
Answer: A
Explanation:
Steps of Implementing Port Security:
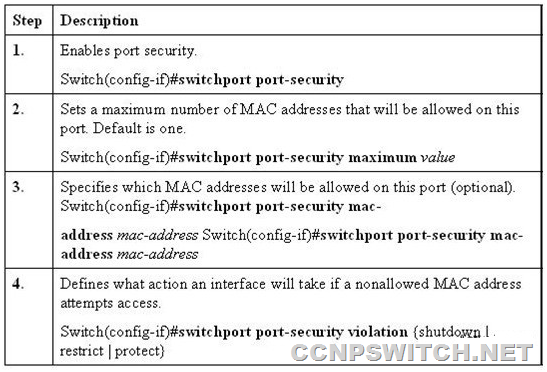
In Exhibit two MAC addresses are allowed so that host will be allowed to connect.
QUESTION NO: 4
Refer to the exhibit. How will interface FastEthernnet0/1 respond when an 802.1x-enabled client connects to the port?
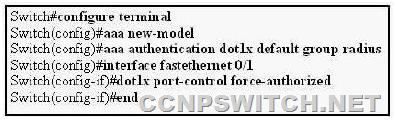
A. The switch will uniquely authorize the client by using the client MAC address.
B. The switch will cause the port to remain in the unauthorized state, ignoring all attempts by the client to authenticate.
C. The switch port will disable 802.1x port-based authentication and cause the port to transition to the authorized state without any further authentication exchange.
D. The switch port will enable 802.1x port-based authentication and begin relaying authentication messages between the client and the authentication server.
Answer: C
Explanation:
The IEEE 802.1x standard defines a port-based access control and authentication protocol that restricts unauthorized workstations from connecting to a LAN through publicly accessible switch ports. The authentication server authenticates each workstation that is connected to a switch port before making available any services offered by the switch or the LAN. Until the workstation is authenticated, 802.1x access control allows only Extensible Authentication Protocol over LAN (EAPOL) traffic through the port to which the workstation is connected. After authentication succeeds, normal traffic can pass through the port.
You control the port authorization state by using the dot1x port-control interface configuration command and these keywords:
force-authorized : Disables 802.1x port-based authentication and causes the port to transition to the authorized state without any authentication exchange required. The port transmits and receives normal traffic without 802.1x-based authentication of the client. This is the default setting.
force-unauthorized : Causes the port to remain in the unauthorized state, ignoring all attempts by the client to authenticate. The switch cannot provide authentication services to the client through the interface.
auto : Enables 802.1x port-based authentication and causes the port to begin in the unauthorized state, allowing only EAPOL frames to be sent and received through the port. The authentication process begins when the link state of the port transitions from down to up (authenticator initiation) or when an EAPOL-start frame is received (supplicant initiation). The switch requests the identity of the client and begins relaying authentication messages between the client and the authentication server. The switch uniquely identifies each client attempting to access the network by using the client MAC address.
Example: 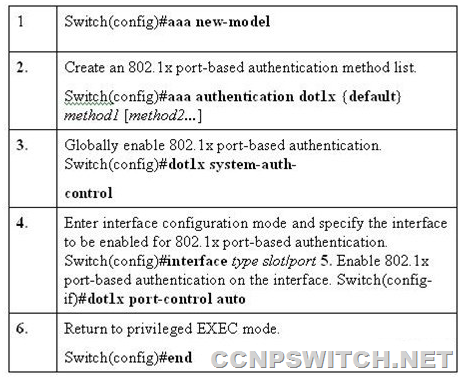
QUESTION NO: 5
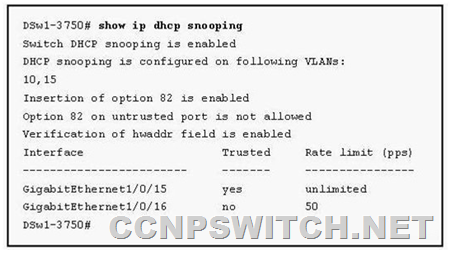
Refer to the exhibit. What type of attack is being defended against?
A. snooping attack
B. rogue device attack
C. STP attack
D. VLAN attack
E. spoofing attack
F. MAC flooding attack
Answer: E
Explanation:
When DHCP snooping is configured, you can display its status with the following command:
Switch#show ip dhcp snooping [binding]
You can use the binding keyword to display all the known DHCP bindings that have been overheard. The switch maintains these in its own database.
A switch can use the DHCP snooping bindings to prevent IP and MAC address spoofing attacks.
MAC spoofing attacks consist of malicious clients generating traffic by using MAC addresses that do not belong to them. IP spoofing attacks are exactly like MAC spoofing attacks, except that the client uses an IP address that isn’t his.

In the question 2 answer “E” can not be correct, because “it is in protect mode — not shutdown”.
Am I right?
Yes, no second choice is valid from that list. 🙄
yes u are Werewolf.
right…
Option E is not correct as 10 MAC addresses are allowed and it would work with ten but when another host connects it would lead to port down.